Privacy Overview
| Cookie | Duração | Descrição |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
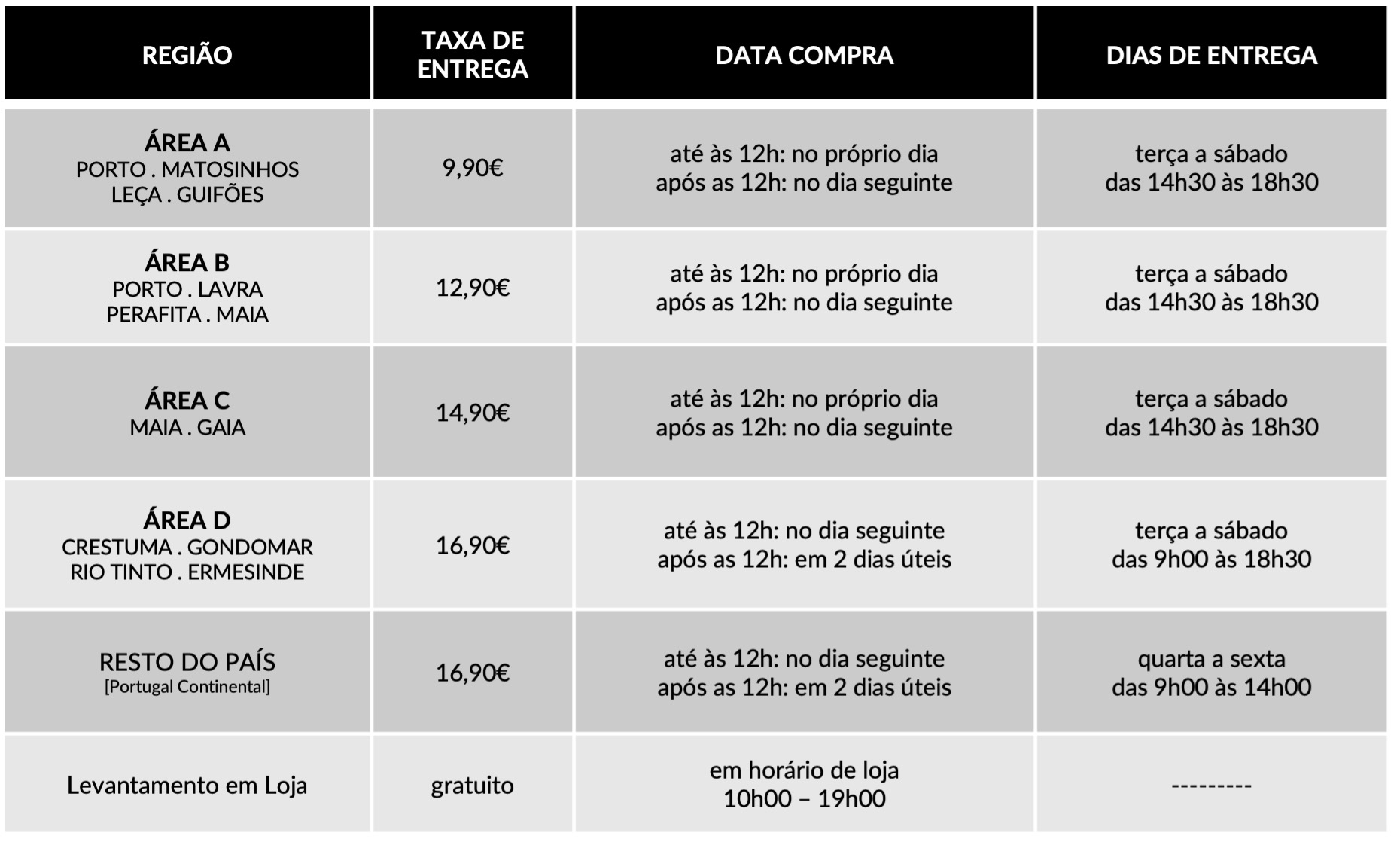
Dedicamos toda a atenção na manutenção e preservação das nossas Flores, garantindo que cheguem ao nosso cliente com toda a frescura, qualidade e beleza. Disponibilizamos várias soluções de manutenção e embalamentos adequando sempre a cada necessidade e contexto da entrega.
Pode incluir na sua oferta uma mensagem personalizada que irá ser reproduzida por nós. No processo da compra online basta preencher o campo ”dedicatória” e escrever a mensagem pretendida.
Valorizamos e priorizamos a qualidade dos serviços e dos nossos produtos. Todas as flores disponibilizadas nos ramos e arranjos disponíveis na loja online são frescas e estão em condições de servir o destinatário.
Caso haja alguma insatisfação por parte do cliente, recomendamos que utilize os nossos canais de comunicação para que possamos analisar a questão.
As fotografias são ilustrativas, quer isto dizer que não garantimos a 100% a sua fieldade com a realidade.
As fotografias devem ser interpretadas como uma base de modelo ou de estética onde as alterações estão sujeitas ao stock da flor e ao trabalho humano de cada florista. Note-se que algumas flores são sazonais e não estão disponíveis todo o ano. Como tal, serão necessárias fazer adaptações consoante a época e o stock da flor.
Para casos onde as alterações sejam extremamente notórias, contactaremos o cliente para ajustar a melhor solução.
Não cancelamos nem alteramos encomendas se esta já se encontrar em fase de curso, ou seja, se já tiver saído da loja e em fase de transporte.
Se a encomenda se encontrar no estado inicial, de processo, é possível alterar e cancelar a encomenda e reaver o seu dinheiro.
Caso não havendo outra referência dada pelo utilizador (por exemplo: deixar no porteiro, na loja x, à pessoa y) o utilizador será contactado de imediato para ficar ao corrente da situação e, à falta de alternativas, a encomenda voltará para a Terrárea, Caso seja reagendada uma nova entrega será cobrada novamente taxa de entrega.
Sublinhamos a importância dos dados fornecidos pelo utilizador estarem correctos e claros. Há sempre a possibilidade do utilizador acrescentar um ponto de referência e outras informações para que não hajam quaisquer dúvidas no acto da entrega garantindo, assim, a qualidade do serviço.
Lamentamos mas não podemos facultar essa informação, se o cliente que realizou a encomenda não pretender.
Estamos abertos a alterações embora estas estejam sempre condicionadas pelo tipo de pedido do utilizador, stock em loja e conceito estético. Nestes casos sugerimos o contacto telefónico ou por email.
Queremos satisfazer todos os nossos clientes e oferecer o nosso melhor serviço. Agradecemos, por isso, todas as opiniões e sugestões para podermos encontrar soluções às suas necessidades! Contacte-nos a partir dos seguintes meios: via email info@terrarea.pt ou telefone 223 170 414
You can see how this popup was set up in our step-by-step guide: https://wppopupmaker.com/guides/auto-opening-announcement-popups/
Ao subscrever a newsletter aceito o tratamento de dados pessoais segundo as políticas de privacidade.
SIGA-NOS EM
CONTACTOS
223 170 414
(Chamada para a rede fixa nacional)
INFO@TERRAREA.PT
COMERCIAL@TERRAREA.PT
How to Lock Down Token Approvals: Practical DeFi Security for Multi‑Chain Wallet Users
Whoa! This topic is messier than most guides let on. My gut said “just revoke approvals,” but that felt incomplete. Initially I thought blanket revocations were the safest move, but then I realized that revoking everything can break recurring interactions with smart contracts you actually trust—like staking or vesting contracts that expect allowances. So here we are: a pragmatic, risk‑aware approach to managing token approvals across chains.
Okay, so check this out—token approvals are the most persistent attack surface in DeFi. Seriously? Yes. When you approve a contract to spend your ERC‑20 (or equivalent) token, you give it the right to move tokens on your behalf until you revoke or change that permission. That permission model is powerful. It’s also dangerous when left unchecked, because malicious or compromised contracts can siphon funds without any further prompt from you.
Here’s the blunt takeaway: approvals are implicit power. You might interact with a DEX once, and the DEX’s router keeps permission to move tokens forever unless you change it. That single convenience call can become long‑term exposure. My instinct said revoke every approval immediately. But actually, wait—there’s nuance. Many legitimate workflows need persistent allowances to operate smoothly, and unnecessary churn creates friction and on‑chain costs.
So how do you balance safety with usability? Use three principles: least privilege, visibility, and automated hygiene.
Least privilege first. Limit approvals to the minimal amount required. If you only need to swap 200 USDC, approve 200 USDC. That reduces worst‑case loss drastically. Medium‑term or recurring flows (subscriptions, yield strategies) are the exception; there you can provision higher allowances to avoid frequent transactions, but keep them scoped to specific addresses rather than blanket approvals wherever possible.
Visibility matters. You can’t manage what you can’t see. Many wallets hide approvals deep inside settings, or they present them as raw permit data that’s hard to parse. That’s why tooling with a clear “token approvals” dashboard is invaluable; you want a single screen that lists every contract with allowance, per chain, with amounts and last interaction timestamps. If you’re using a multi‑chain wallet, that dashboard should span chains so you don’t miss a forgotten approval on Polygon while focusing on Ethereum.
Automated hygiene comes next. Tools that suggest risky approvals, highlight infinite allowances, and batch revokes (with gas optimization heuristics) are worth adopting. But caution: automation must be consented. Some batch revoke flows use allowance reset patterns that cost gas and occasionally fail on certain tokens (rebase, fee‑on‑transfer, or poorly implemented tokens). Test on small amounts first, and always review the target contract address (copy/paste, do not trust clickable links in unknown dapps).
On the subject of infinite approvals—ugh, that part bugs me. Infinite (or “max”) approvals are the default on many DEX UIs to save clicks. They simplify UX, but they also convert a one‑time convenience into an ongoing open door. If a dapp’s backend is compromised, the attacker can drain unlimited tokens. My bias is against max approvals unless you’re interacting repeatedly with a very reputable contract and you understand the tradeoffs. For casual swaps, explicit limited approvals are better.
Practical checklist—short and actionable:
1. Audit allowances monthly (or more often if you trade frequently).
2. Revoke or reduce unnecessary allowances—start with infinite approvals.
3. Favor per‑transaction limited approvals for one-off swaps.
4. Whitelist and maintain allowances for trusted contracts only.
5. Use hardware wallets or strong device compartmentalization for high‑value accounts.
How a multi‑chain wallet like rabby helps
I started using tools that make approvals obvious, not hidden. One wallet that gets this right is rabby, which surfaces approvals across EVM chains, highlights infinite allowances, and provides convenient revoke flows. That single view saved me from a sloppy mistake where I had left a large USDC allowance granted to an obscure router on a testnet‑like chain (oh, and by the way—testnet addresses sometimes get reused in poorly audited bridges). Rabby also supports hardware wallet integration and per‑site permissions, which reduces blast radius when a web dapp misbehaves.
Beyond tooling, use workflow patterns that reduce exposure. When possible, proxy your interactions through a smart contract you control (a personal vault or a multi‑sig). That way, you centralize approvals to a contract with constrained logic rather than scattering allowances across dozens of third‑party contracts. Sounds complex? It can be. But for serious capital, it’s worth the engineering cost.
Another tactic: time‑bound approvals. Some contracts support permits or signed approvals that expire; leverage these where available. They give you the convenience of off‑chain approval while removing perpetual exposure. Also look for protocols that implement ERC‑20 permit (EIP‑2612) or similar—these can reduce gas and allow finer control without on‑chain allowance persistence.
On the operational security side, compartmentalize assets. Keep a “hot” wallet for day‑to‑day swaps and a “cold” wallet for long‑term holdings. Use different seed phrases. If a hot wallet encounters a malicious contract, the potential loss is limited by design. Yeah, it’s extra steps. But I’d rather pay a little UX friction than wake up to a drained account.
Be skeptical of approvals requested via confusion tactics. Phishing dapps will sometimes present familiar UIs but with different contract addresses or subtly modified routing logic. My red flag checklist: mismatched domain names, requests for approvals immediately after connecting without a clear UX, and approvals that reference proxy contracts rather than direct DEX routers. If somethin’ feels off, pause and fetch the contract address from the protocol’s GitHub or verified sources.
Finally, keep gas strategies in mind. Revoking allowances costs gas. If you batch revokes across ten chains at once you’ll pay. Consider a prioritized approach: revoke the riskiest (infinite allowances to unknown contracts) first. Use gas‑saver features in wallets where available, and for small allowances, weigh the gas cost against the exposure—the math matters.
FAQ
How often should I check my token approvals?
Monthly for most users. Weekly if you’re an active trader. Immediately after you interact with a new dapp you care about. Automated alerts (via tooling or wallet notifications) make this less painful.
Is revoking an approval safe for all tokens?
Mostly yes, but some tokens are quirky (rebasing tokens, fee‑on‑transfer, or non‑standard ERC implementations). Test revokes on small amounts first. When in doubt, consult the token’s docs or the community; and avoid blind mass revokes on chains where you hold complex positions.