Privacy Overview
| Cookie | Duração | Descrição |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
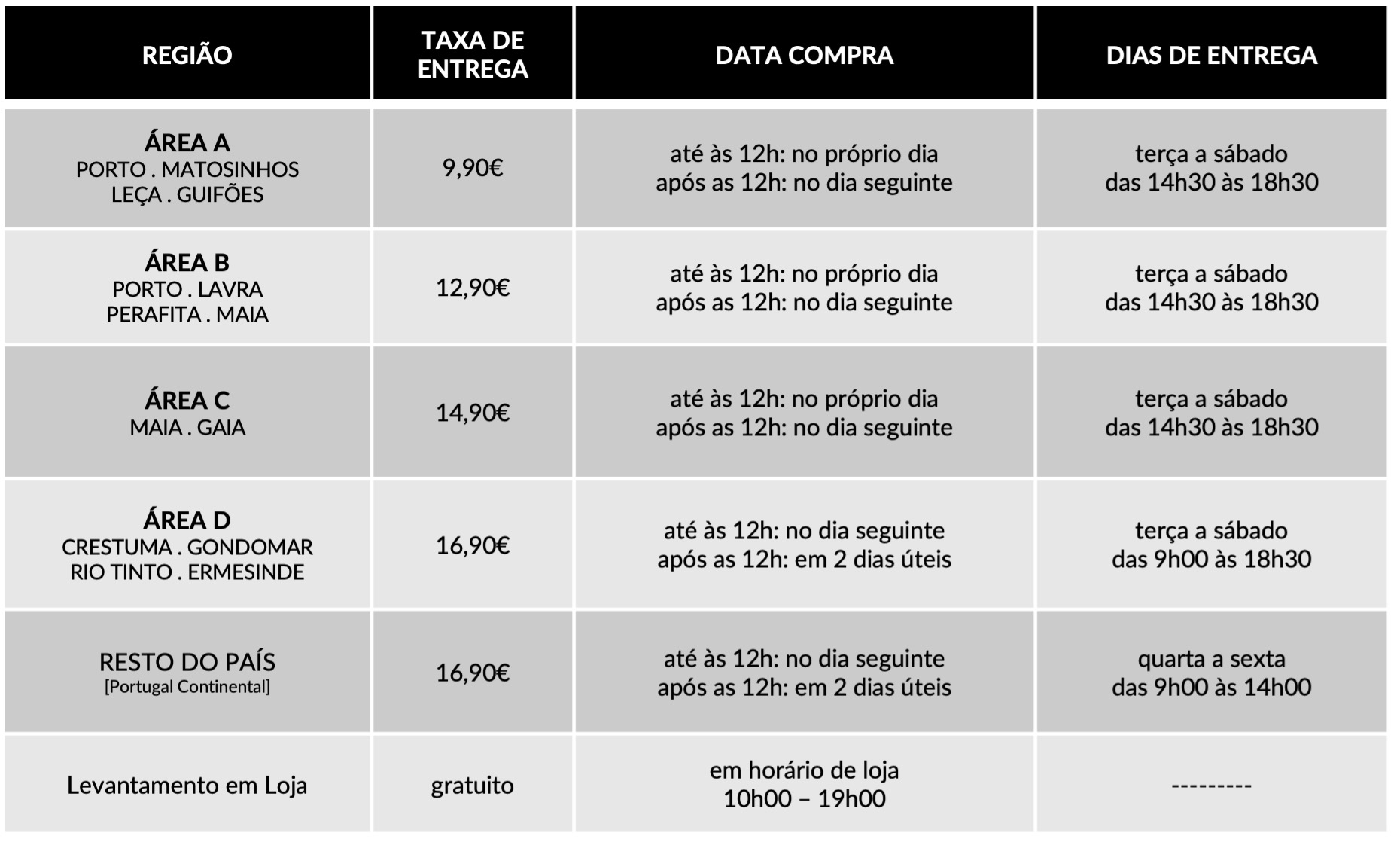
Dedicamos toda a atenção na manutenção e preservação das nossas Flores, garantindo que cheguem ao nosso cliente com toda a frescura, qualidade e beleza. Disponibilizamos várias soluções de manutenção e embalamentos adequando sempre a cada necessidade e contexto da entrega.
Pode incluir na sua oferta uma mensagem personalizada que irá ser reproduzida por nós. No processo da compra online basta preencher o campo ”dedicatória” e escrever a mensagem pretendida.
Valorizamos e priorizamos a qualidade dos serviços e dos nossos produtos. Todas as flores disponibilizadas nos ramos e arranjos disponíveis na loja online são frescas e estão em condições de servir o destinatário.
Caso haja alguma insatisfação por parte do cliente, recomendamos que utilize os nossos canais de comunicação para que possamos analisar a questão.
As fotografias são ilustrativas, quer isto dizer que não garantimos a 100% a sua fieldade com a realidade.
As fotografias devem ser interpretadas como uma base de modelo ou de estética onde as alterações estão sujeitas ao stock da flor e ao trabalho humano de cada florista. Note-se que algumas flores são sazonais e não estão disponíveis todo o ano. Como tal, serão necessárias fazer adaptações consoante a época e o stock da flor.
Para casos onde as alterações sejam extremamente notórias, contactaremos o cliente para ajustar a melhor solução.
Não cancelamos nem alteramos encomendas se esta já se encontrar em fase de curso, ou seja, se já tiver saído da loja e em fase de transporte.
Se a encomenda se encontrar no estado inicial, de processo, é possível alterar e cancelar a encomenda e reaver o seu dinheiro.
Caso não havendo outra referência dada pelo utilizador (por exemplo: deixar no porteiro, na loja x, à pessoa y) o utilizador será contactado de imediato para ficar ao corrente da situação e, à falta de alternativas, a encomenda voltará para a Terrárea, Caso seja reagendada uma nova entrega será cobrada novamente taxa de entrega.
Sublinhamos a importância dos dados fornecidos pelo utilizador estarem correctos e claros. Há sempre a possibilidade do utilizador acrescentar um ponto de referência e outras informações para que não hajam quaisquer dúvidas no acto da entrega garantindo, assim, a qualidade do serviço.
Lamentamos mas não podemos facultar essa informação, se o cliente que realizou a encomenda não pretender.
Estamos abertos a alterações embora estas estejam sempre condicionadas pelo tipo de pedido do utilizador, stock em loja e conceito estético. Nestes casos sugerimos o contacto telefónico ou por email.
Queremos satisfazer todos os nossos clientes e oferecer o nosso melhor serviço. Agradecemos, por isso, todas as opiniões e sugestões para podermos encontrar soluções às suas necessidades! Contacte-nos a partir dos seguintes meios: via email info@terrarea.pt ou telefone 223 170 414
You can see how this popup was set up in our step-by-step guide: https://wppopupmaker.com/guides/auto-opening-announcement-popups/
Ao subscrever a newsletter aceito o tratamento de dados pessoais segundo as políticas de privacidade.
SIGA-NOS EM
CONTACTOS
223 170 414
(Chamada para a rede fixa nacional)
INFO@TERRAREA.PT
COMERCIAL@TERRAREA.PT
Why I Trust My Privacy Wallets (And Why You Should Care)
Whoa! I was just messing around with wallets last week when somethin’ hit me: privacy isn’t an add-on anymore. It’s the table stakes. Seriously? Yep. We live in a world where your on-chain habits can be stitched together if you squint the right way. So let’s talk about what works, what doesn’t, and how to think about Bitcoin and Monero wallets without getting lost in techno-jargon.
Here’s the thing. At first glance, Bitcoin and Monero look like siblings — both crypto, both digital. But the resemblance is skin-deep. Bitcoin gives you pseudonymity; you get addresses and transactions that are public by design. Monero, on the other hand, was built to hide. Cryptography like ring signatures and stealth addresses does heavy lifting there, and that changes how you choose a wallet. Initially I thought choosing a wallet was mostly about UX and convenience, but then I realized the trade-offs are deeper. They involve network privacy, node trust, and the subtle ways wallets leak metadata.
Quick gut take: if you care about privacy, noncustodial is a must. No exceptions. My instinct said “avoid custodial wallets” the moment I started tracking what happens when third parties control keys. On one hand, custodial services offer convenience. On the other hand, they have liability, subpoenas, and keystores. Honestly—I’m biased, but handing your keys to an exchange or app is handing them a map to your life.
Short and blunt: hardware for large sums. Software for daily use. Medium-term: split funds across strategies. Long game: run your own node if you can, or at least use wallets that support one. It sounds pedantic, though actually it matters more than most people realize because metadata trumps math in many real-world deanonymization cases.
Bitcoin wallets — privacy tips that actually help
Okay, so check this out—Bitcoin’s privacy depends heavily on patterns. Mixed inputs, repeated addresses, reused change addresses… these little habits create a breadcrumb trail. Use native segwit addresses when possible for lower fees, sure. But privacy-wise, avoid address reuse. Really. Seriously. CoinJoins and mixers help if done correctly, though they introduce complexity and sometimes legal gray areas.
One big nuance: some wallets expose your IP to peers. That alone can connect your transactions to your device. Initially I recommended light wallets that use public servers, but then I realized I was exposing people to network-level leaks. Actually, wait—let me rephrase that: light wallets are fine when paired with privacy-preserving networks like Tor or I2P, or when the wallet supports connecting to your own Electrum or Bitcoin Core node. On one hand, easy setups boost adoption. On the other, easy setups often sacrifice privacy.
Here’s a practical checklist for Bitcoin privacy in wallets: use coin-control features, prefer wallets that let you run or connect to your own node, enable Tor for peer connections, and consider CoinJoin tools if you need stronger plausible deniability. I won’t pretend mixing is foolproof. There are failures and deanonymization studies. But used intelligently, these tools raise the cost of surveillance.
Monero wallets — privacy by design, but not problem-free
Monero is different. Its default privacy primitives—ring signatures, stealth addresses, and confidential transactions—mean transaction graphs are obfuscated by default. That sounds perfect, and it often is, but it’s not a “set and forget” solution. Your metadata choices still matter. For example, reuse of payment IDs (yeah, some wallets and services still do this) or careless IP exposure can leak.
My experience with Monero wallets taught me something subtle. Initially I trusted light wallets for convenience. Then I realized the trade-off: light wallets usually require remote nodes, and remote nodes can correlate requests. So running your own node or choosing wallets that support remote node encryption via SSL/TLS or Tor matters a lot. On the other hand, self-hosting a node is heavy for many users, so balance matters.
Want a practical path? Use a reliable Monero wallet that gets regular audits and updates. Pair it with Tor, or use a remote node you trust. And watch out for exchanges or services that leak KYC data—private on-chain coin doesn’t help if your fiat on-ramp requires identity. I’m not 100% sure every service will keep your data safe, so I keep some funds off the KYC rails.
Wallet choice: UX, security, and privacy trade-offs
Wow! Wallet choice is often about compromises. Mobile wallets are convenient. Desktop wallets are flexible. Hardware wallets are sanctuaries for large holdings. The trick is matching threat models to tools. If someone in the U.S. reading this cares about casual privacy—like avoiding ad surveillance—then a privacy-focused mobile wallet plus Tor might be fine. If you’re a journalist or activist with higher risk, then hardware, full nodes, and strict OPSEC are needed.
One practical recommendation I sometimes share with friends: test small transfers first. Use small amounts to learn the flow before moving larger sums. And if you want a no-nonsense download link for a multiservice wallet, check this out—get the app here. It’s not a silver bullet, but it’s a starting point if you want multi-currency support with privacy features.
I’ll be honest: some parts of this industry bug me. Wallet vendors sometimes over-promise anonymity, or they slip into dark UX patterns that confuse users into less-safe setups. (Oh, and by the way…) vendor reputation matters. Look for open-source code, active audits, and an engaged developer community. Those aren’t guarantees, but they tilt odds in your favor.
Common mistakes people make
Really? Reusing addresses is still the top sin. Close second: mixing signals across chains. For example, if you try to privacy-cover Bitcoin transactions but then move the same funds into a KYC exchange, all bets are off. People also underestimate device-level leaks: browser extensions, SIM swaps, and cloud backups can expose seeds. Use strong passphrases and resist cloud backups for seed phrases unless encrypted and deliberate.
On the technical side, some users assume privacy features are binary. They aren’t. It’s a spectrum. Your threat model, habits, and environment define how private you are. That means you must think like an analyst sometimes. Initially I thought “use the tool and you’re fine.” But the more cases I saw, the more nuance I needed to accept.
FAQ
Can Bitcoin be made as private as Monero?
Short answer: not by default. Bitcoin can be privacy-enhanced with techniques like CoinJoin, careful wallet hygiene, and network protections (Tor), but Monero hides transaction graphs by design. That said, a disciplined Bitcoin user can achieve strong privacy for many threat models, though it’s typically harder and requires more operational care.
Should I run my own node?
Yes, if you can. Running a node reduces trust in others and avoids leaking metadata to remote servers. It’s the gold standard for privacy. But if you can’t, use wallets that support Tor and let you connect to trusted nodes—it’s better than nothing.
Is a hardware wallet necessary?
For large holdings, absolutely. Hardware wallets protect your private keys from host compromise. For everyday small transactions, secure mobile/desktop wallets are fine, but keep backups and use strong device hygiene.
My final thought—well, not final exactly, but for now: privacy is a habit as much as a technology. It requires continuous attention, small annoyances, and occasional sacrifices for convenience. Something felt off when people treated privacy like a toggle. It’s not. Protecting your financial privacy is an ongoing practice. Stay curious. Stay skeptical. And don’t hoard everything in one place—diversify, practice, and learn from mistakes. Someday we’ll have better defaults. Until then, be deliberate.