Privacy Overview
| Cookie | Duração | Descrição |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
Dedicamos toda a atenção na manutenção e preservação das nossas Flores, garantindo que cheguem ao nosso cliente com toda a frescura, qualidade e beleza. Disponibilizamos várias soluções de manutenção e embalamentos adequando sempre a cada necessidade e contexto da entrega.
Pode incluir na sua oferta uma mensagem personalizada que irá ser reproduzida por nós. No processo da compra online basta preencher o campo ”dedicatória” e escrever a mensagem pretendida.
Valorizamos e priorizamos a qualidade dos serviços e dos nossos produtos. Todas as flores disponibilizadas nos ramos e arranjos disponíveis na loja online são frescas e estão em condições de servir o destinatário.
Caso haja alguma insatisfação por parte do cliente, recomendamos que utilize os nossos canais de comunicação para que possamos analisar a questão.
As fotografias são ilustrativas, quer isto dizer que não garantimos a 100% a sua fieldade com a realidade.
As fotografias devem ser interpretadas como uma base de modelo ou de estética onde as alterações estão sujeitas ao stock da flor e ao trabalho humano de cada florista. Note-se que algumas flores são sazonais e não estão disponíveis todo o ano. Como tal, serão necessárias fazer adaptações consoante a época e o stock da flor.
Para casos onde as alterações sejam extremamente notórias, contactaremos o cliente para ajustar a melhor solução.
Não cancelamos nem alteramos encomendas se esta já se encontrar em fase de curso, ou seja, se já tiver saído da loja e em fase de transporte.
Se a encomenda se encontrar no estado inicial, de processo, é possível alterar e cancelar a encomenda e reaver o seu dinheiro.
Caso não havendo outra referência dada pelo utilizador (por exemplo: deixar no porteiro, na loja x, à pessoa y) o utilizador será contactado de imediato para ficar ao corrente da situação e, à falta de alternativas, a encomenda voltará para a Terrárea, Caso seja reagendada uma nova entrega será cobrada novamente taxa de entrega.
Sublinhamos a importância dos dados fornecidos pelo utilizador estarem correctos e claros. Há sempre a possibilidade do utilizador acrescentar um ponto de referência e outras informações para que não hajam quaisquer dúvidas no acto da entrega garantindo, assim, a qualidade do serviço.
Lamentamos mas não podemos facultar essa informação, se o cliente que realizou a encomenda não pretender.
Estamos abertos a alterações embora estas estejam sempre condicionadas pelo tipo de pedido do utilizador, stock em loja e conceito estético. Nestes casos sugerimos o contacto telefónico ou por email.
Queremos satisfazer todos os nossos clientes e oferecer o nosso melhor serviço. Agradecemos, por isso, todas as opiniões e sugestões para podermos encontrar soluções às suas necessidades! Contacte-nos a partir dos seguintes meios: via email info@terrarea.pt ou telefone 223 170 414
You can see how this popup was set up in our step-by-step guide: https://wppopupmaker.com/guides/auto-opening-announcement-popups/
Ao subscrever a newsletter aceito o tratamento de dados pessoais segundo as políticas de privacidade.
SIGA-NOS EM
CONTACTOS
223 170 414
(Chamada para a rede fixa nacional)
INFO@TERRAREA.PT
COMERCIAL@TERRAREA.PT
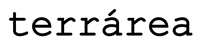
Why your next mobile wallet should think like a security engineer (not just a product designer)
Whoa, this is wild. Mobile wallets are finally getting serious about cross-chain usability and real security. That feels overdue given how messy tokens and bridges have been. At first glance it’s tempting to trust the slick UX, but underneath those smooth animations are complex trust assumptions and silent risks that most people do not understand yet. I’ll walk through what to look for when you move assets across chains.
Hmm, not all wallets are equal. My instinct said the shiny interface hides permission creep and hidden approvals. On one hand designers simplify flows; though actually that can hide approvals. Initially I thought wallets could just be prettier interfaces around the same seed phrase model, but after digging I realized the differences in key management, session signing, and RPC routing materially change your risk profile. There are trade-offs and I want to be clear about them.
Seriously, bridges are tricky. Atomic swaps, trusted relays, and liquidity pools each have different failure modes you should know. Beware of approved allowances that outlive the transaction and of multisig schemes that are superficially decentralized. If a bridge operator has a choke point or a hot key, or if a smart contract has a recover function, your assets can be frozen or siphoned even when the UI says “bridge complete” and your balance updates immediately. So read the warnings, check contracts, and don’t assume the dashboard tells the whole truth.
Wow, hardware matters. Mobile secure enclaves, biometric wraps, and OS-level keystores are not all equivalent. A wallet that claims “secure” but exports keys to an insecure browser context is suspect. I’m biased, but I prefer wallets that isolate signing in a hardened module while letting the app handle presentation only, because that separation reduces attack surface in practical terms even if it complicates UX a bit. You should test transaction signing flows before trusting large amounts (oh, and by the way… keep a notebook of what each approval actually did).
Hmm, multisig helps a lot. Multisig splits authority, which is great, though it brings coordination friction during recovery. Social recovery models reduce single-point-of-failure but can introduce social engineering risk. Consider hybrid approaches: use a multisig for high value holdings, a daily-use account for small spends, and a cold key backup stored offline with redundancy in different jurisdictions, because real-world availability matters. Practice your recovery before you need it; broken processes are the real threat.
Okay, so check this out— EIP-712 signed messages let wallets show human-readable payloads, which is huge for preventing phishing. But many wallets still fall back to raw hex, or omit warnings for unlimited approvals. Cross-chain UX should also expose which validators or relayers are being used, what slippage tolerance you’re consenting to, and whether wrapped tokens are custodial or fully composable on the destination chain, because those details affect both cost and counterparty risk. If a wallet hides routing choices, you lose auditability and leverage as a user. That loss becomes very very important when markets move fast.
Really, permissions galore. Disconnecting sessions, revoking approvals, and revoking RPC access are basic hygiene steps many skip. Connectors that keep session tokens lingering are quietly dangerous in practice. Use wallets that give you granular control over approval lifetimes and that allow selective chain whitelisting, because blanket approvals are how billions in value get drained during clever phishing campaigns. Audit and prune approvals regularly, even somethin’ as small as a token allowance can be exploited.
I’m not shilling here. But I’ve tried many apps and have a clear checklist for picks. Look for clear RPC sourcing, on-device signing, session controls, open-source audits, and simple recovery options. A wallet that focuses on multichain management and transparent signing practices can reduce mental load, though no wallet removes all risk and you should still diversify custody for large holdings. Always test with small amounts, and treat integration with dApps as a constant experiment.
Whoa, watch gas spikes. Use reputable bridges, avoid brand-new bridge releases, and prefer audited contracts with bug bounties. Be mindful of slippage and front-running potential during high volume. If you route across multiple bridges and autonomous relayers, track each hop’s custody assumptions, because one intermediary can reconstitute holdings and defeat the purpose of decentralization. And yes, small amounts for testing are your friend.
Okay, here’s the practical bit. Link hardware wallets when possible and use them for high-value multisig keys. Keep hot wallets for day-to-day use, and cold wallets for reserves. I still get nervous about new smart contracts and my recommendation is to separate operational funds from treasury holdings, automate small recurring transfers for yields, and keep documentation of all recovery steps in a secure place that a trusted executor can access in emergencies. I’m ending here slightly more cautious but also more equipped; that feels right.
A short, practical checklist and a wallet to try
If you want a starting point, check wallets that clearly state their RPC providers, show human-readable EIP-712 payloads, isolate signing, and make it trivial to revoke approvals. One option that aligns with these priorities is truts, which emphasizes multichain management and transparent signing practices; test it with tiny transfers first and see how its session controls behave. Remember: tools help, but habits matter more—revoke, test, and diversify.
FAQ
How should I test a new wallet?
Start with a small amount that you can afford to lose, execute a cross-chain transfer, check contract addresses on a block explorer, inspect EIP-712 payloads during signing, and then revoke the approval. Repeat the flow a few times; broken UX often hides inconsistent behavior that only shows up after repeated use.
Are mobile wallets safe enough for serious holdings?
They can be, with proper setup: hardware-backed signing, multisig for large holdings, segregated hot/cold accounts, and tested recovery procedures. Still, for very large treasuries, cold storage with geographically distributed backups remains the least risky option.
What’s the single biggest user mistake?
Blindly approving unlimited allowances and trusting a dashboard without checking contract details. That one move is how attackers automate drains; you can avoid it by setting limited allowances and using wallets that alert you to risky approvals.